Your Business Runs on Phones. Treat them like Primary Endpoints.
What You Need to Know
Mobile devices are now the primary entry point for attackers. Canadian small and mid‑sized businesses (SMBs) rely on smartphones and tablets for approvals, payments, messaging, customer service, and multifactor authentication (MFA). That makes mobile the front door to your data, revenue, and reputation. Traditional desktop tools cannot see smishing (SMS phishing), malicious software development kits (SDKs) inside otherwise legitimate apps, man‑in‑the‑middle attacks on public Wi‑Fi, or “zero‑click” exploits that silently place spyware on a device.
This article shows how to close the gap with a complete mobile security programme: Mobile Device Management/Unified Endpoint Management (MDM/UEM) for control and compliance; Mobile Threat Defence (MTD) for on‑device detection and automated response; phishing‑resistant authentication (passkeys/FIDO2) to replace SMS codes; Zero Trust access; privacy‑respecting BYOD; and mobile‑aware incident response. Aligned to PIPEDA and Québec’s Law 25, the plan is practical, budget‑aware, and measurable.
Outcome: Fewer incidents, faster containment, lower regulatory exposure, and resilient operations—without slowing your teams down.
Why Mobile Security Matters Now
Your business runs on mobile. Executives approve payments from phones. Sales reps carry quotes and contracts in chat threads. Field teams upload photos and videos from job sites. Many staff authenticate to cloud systems with one‑time codes delivered by SMS.
Attackers follow the value. Smishing and mobile‑optimized phishing kits now imitate banks, parcel services, payroll providers, and even MFA prompts. Malicious SDKs embedded in popular apps can harvest data despite being downloaded from official stores. Spyware campaigns and one‑tap exploits allow remote monitoring of calls, messages, location, camera, and microphone. Network‑level attacks on open Wi‑Fi or spoofed hotspots intercept traffic and hijack sessions.
For owners and executives, the business impact is straightforward: a single compromised device can lead to account takeover, wire fraud, data exfiltration, and mandatory breach notifications. Insurers increasingly assess mobile controls when underwriting. Clients and partners expect you to show due diligence. If you treat mobile as an afterthought, you inherit a disproportionate share of risk.
The Modern Mobile Threat Landscape
Smishing and mobile phishing. Small screens obscure full URLs and security indicators. AI‑written text messages and in‑app pop‑ups look authentic. QR codes push users to fake portals that steal credentials or initiate rogue payments.
Spyware and zero‑click exploits. Advanced attackers target leaders, finance teams, journalists, and policy stakeholders. Exploits require no user action and can silently exfiltrate files, read messages, and activate sensors.
App supply‑chain risks. Attackers tamper with SDKs or compromise developer accounts so malicious code ships inside legitimate updates—even via official stores—turning trusted apps into data harvesters until vendors discover and remove them.
Network‑based attacks. Rogue access points, cellular downgrades, and TLS‑stripping capture credentials and session cookies. Users on public networks are particularly exposed.
MFA interception and session theft. On‑device malware can read one‑time passcodes, forward push prompts, or steal cookies to take over accounts without passwords.
Configuration abuse. Unapproved configuration profiles, sideloaded apps, and debugging settings create blind spots for IT and open doors for attackers.
Business Risks of Unprotected Mobile Devices
- Data exfiltration: Customer lists, pricing, contracts, design files, and regulated personal information leave the organization without detection.
- Operational disruption: Remote wipes, device locks, or stolen sessions halt approvals, payroll, and field operations.
- Financial loss: Business email compromise (BEC), invoice manipulation, and fraudulent payment redirects often start with a mobile account takeover.
- Regulatory exposure: PIPEDA and Law 25 require breach logs and, in many circumstances, notifications. Failing to show reasonable safeguards increases fines and legal exposure.
- Insurance friction: Weak controls lead to higher premiums, exclusions, or denied claims.
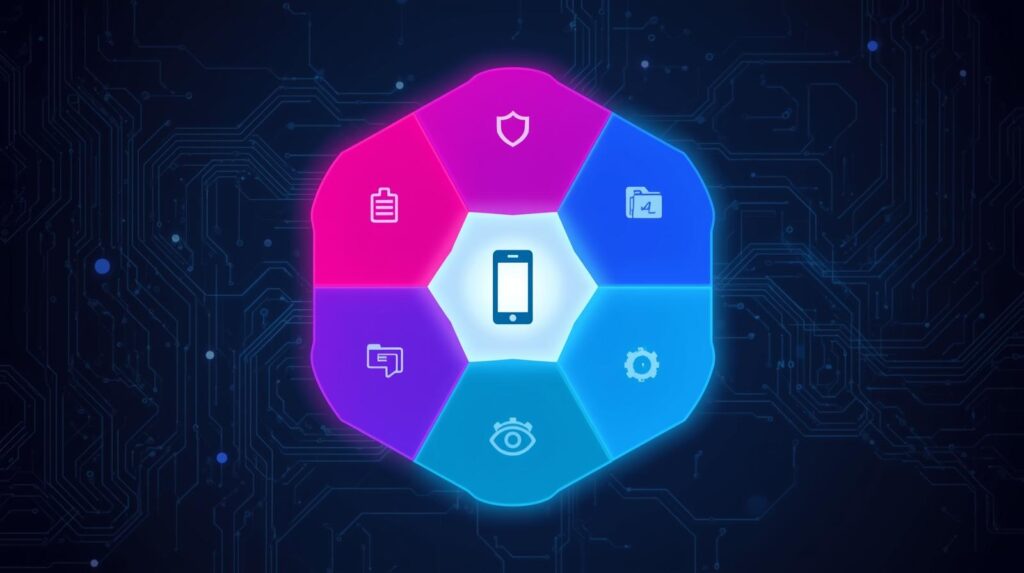
What “Good” Looks Like: A Mobile Security Reference Architecture
A robust mobile program has six pillars. Each pillar contributes to prevention, detection, and fast recovery.
1) Identity and Access (Make Phishing Hard)
- Phishing‑resistant MFA: Prioritize passkeys or FIDO2 security keys for executives, finance, HR, and admins. Retire SMS codes wherever you control the app.
- Conditional access: Combine user risk, device health (MDM/MTD signals), application sensitivity, geolocation, and network context before granting access. Block rooted/jailbroken devices by default.
- Session management: Shorten session lifetimes for high‑risk apps; require step‑up authentication when risk increases or when a device falls out of compliance.
2) MDM/UEM (Establish Control and Compliance)
- Authoritative inventory: Know every device with access to corporate resources—corporate‑owned, COPE (corporate‑owned, personally enabled), and BYOD. Tag by owner, role, and risk tier.
- Baseline policies: Enforce PIN/biometric, full‑disk encryption, auto‑lock in ≤ 60 seconds, automatic OS/app updates, and minimum OS versions.
- Configuration management: Distribute Wi‑Fi/VPN profiles, blocked/approved app lists, and restrictions on configuration profiles.
- Separation of work and personal: Use Android Enterprise work profiles or iOS managed apps to containerise corporate data while preserving personal privacy.
3) Mobile Threat Defence (See and Stop What Matters)
- On‑device analytics: Detect malicious behaviors, rogue profiles, sideload attempts, risky apps/SDKs, and network anomalies—even when offline.
- Link and content inspection: Score URLs from SMS, chat, email, and QR codes; block or warn before users engage.
- Automated response: When risk crosses a threshold, trigger MDM to quarantine the device, remove the offending app, or block corporate access automatically.
4) Data Protection (Minimize and Monitor)
- Mobile DLP: Restrict copy/paste from managed to personal apps; disable unmanaged backups for work data; limit screenshots in sensitive applications.
- Secure collaboration: Prefer links with expiry and limited scope over file attachments; log and alert on unusual sharing patterns.
- Encryption and keys: Enforce hardware‑backed keystores and encryption at rest for all managed apps.
5) Network Hygiene (Assume Every Network Is Hostile)
- Per‑app or always‑on VPN: Ensure sensitive traffic uses an encrypted channel.
- DNS filtering: Resolve through secure resolvers with policy enforcement; block newly registered or known malicious domains.
- Wi‑Fi trust policies: Disable auto‑join to open networks; prefer mobile data; flag captive portals and spoofed SSIDs.
6) Operations (Visibility, Response, and Culture)
- 24/7 monitoring: Stream MDM and MTD telemetry into your SIEM/XDR. Prioritize alerts by role and exploit severity.
- IR playbooks: Standardize mobile triage, containment, evidence capture, re‑enrolment, and user communications.
- Awareness programs: Offer short, recurring training on smishing, QR scams, travel hygiene, and consent‑based MFA prompts. Reinforce with simulated smishing campaigns.
Implementation Guide: From Zero to Confident
This guide is designed for SMBs with limited time and budgets. You can implement in stages without losing effectiveness.
Step 1: Build the Inventory
Start with your identity provider and email system to enumerate devices accessing corporate resources. Cross‑reference MDM enrolment. Tag devices by owner (corporate vs BYOD), role, and risk tier (executives and finance first). A clean inventory is the foundation for compliance and for insurer questionnaires.
Step 2: Define the Baseline
Publish a short mobile standard: PIN/biometric required; encryption at rest; auto‑lock ≤ 60 seconds; auto‑updates enabled; minimum OS version; no sideloading; block unknown configuration profiles. Communicate that enrolment in MDM and installation of the MTD agent are conditions of access for designated roles.
Step 3: Harden Identity
Replace SMS one‑time codes with passkeys or FIDO2 security keys for high‑risk apps (finance, HR, admin portals). Shorten session lifetimes on mobile and enable risk‑based re‑authentication. Ensure password resets revoke tokens and invalidate sessions.
Step 4: Deploy MDM/UEM
Choose a platform that supports your device mix (iOS, iPad OS, Android) and integrates with your identity provider. Configure profiles for Wi‑Fi, VPN, DNS, and email; enforce minimum OS versions; and build a managed app catalogue. For BYOD, enable work profiles/managed apps to keep corporate data isolated while preserving personal privacy.
Step 5: Add Mobile Threat Defence
Select an MTD solution with on‑device detection and tight integration to MDM and SIEM/XDR. Start with executives, finance, HR, and admins. Test automated quarantine and app removal. Turn on link inspection for SMS, chat, and QR codes. Validate alerts end‑to‑end—from device, to MTD, to SIEM, to the analyst runbook.
Step 6: Secure the Network Path
Implement per‑app VPN for sensitive apps and always‑on VPN for corporate‑owned devices. Enforce DNS filtering and block risky categories (newly registered domains, known malware hosts, and impersonation patterns). Create a travel profile with hardened settings for roaming staff.
Step 7: Educate the Humans
Run a ten‑minute smishing refresher covering: delivery scams, payroll changes, tax notices, and MFA fatigue prompts. Teach the “pause and verify” habit—use a separate channel to confirm requests before acting. Provide one‑page quick guides for iOS and Android on how to check app permissions, revoke profiles, and report suspicious prompts.
Step 8: Instrument and Measure
Define and publish your mobile KPIs (see Metrics section). Review them monthly in your security steering meeting. Use the data to nudge stragglers, prove progress to executives, and satisfy insurer and client requests.
BYOD That Respects Privacy
BYOD (bring your own device) increases adoption and lowers hardware costs, but only if users trust that the company won’t see personal content. The following approach balances privacy and security:
- Clear consent: Enrolment explains what IT can and cannot see. IT sees posture (OS version, compliance status, managed app list) and risk alerts—not personal photos, messages, or browsing history.
- Work/personal separation: Use Android work profiles and iOS managed apps to containerise corporate data. If a device is lost or an employee departs, only the work container is wiped; personal data remains.
- Approved apps only: Provide a managed app store for email, calendar, file storage, chat, and productivity tools. Disallow sideloading and unknown app stores.
- Privacy defaults: Disable diagnostics that could leak personal data from managed apps. Keep logs scoped to what is necessary for security and compliance.
Communicate these points up front. BYOD succeeds when users feel their privacy is respected.
Compliance for Québec Law 25 and PIPEDA
Canadian privacy laws apply to personal information regardless of where it sits—desktop, cloud, or mobile. Make sure your mobile program aligns with the following:
- Breach log: Maintain a central breach register that includes mobile incidents. Record detection time, affected data, user roles, containment actions, and whether notification thresholds are met.
- Data‑protection impact assessments (DPIAs): For mobile apps that collect personal information, document what data is collected, the purpose, retention, and safeguards. Minimise data collection on mobile forms and disable unnecessary telemetry.
- Vendor transparency: Require app and SDK providers to disclose processors, data residency, and sub‑processors. Capture this in your vendor inventory and contracts.
- Access controls: Demonstrate that only compliant devices with authenticated users can access personal data. This is where conditional access and MTD posture checks pay off.
- Notification templates: Prepare customer and regulator notification templates with mobile‑specific guidance (e.g., reset sessions, revoke tokens, rotate keys).
- Audit artefacts: Keep copies of MDM/MTD policies, enrolment rates, patch SLAs, simulation results, and IR playbooks. These demonstrate reasonable safeguards and continuous improvement.
Mobile Incident Response Playbook (Field‑Tested)
Triggers: A user reports clicking a smishing link; repeated MFA prompts appear without action; the MTD agent flags a high‑risk app; an unknown device registers to an account; or logs show a suspicious login following a travel event.
Immediate actions (first 15 minutes):
- Isolate the device via MDM—block corporate apps and network access.
- Reset credentials and revoke sessions for the affected user; rotate application tokens and API keys if necessary.
- Quarantine or remove suspicious apps and profiles; disable risky Wi‑Fi profiles.
- Capture evidence: Export key logs from MDM, MTD, and the identity provider; preserve them with chain‑of‑custody notes.
Eradication and recovery (within 24 hours):
- Patch OS and apps; reimage the device if compromise persists.
- Re‑enroll in MDM and verify device attestation and compliance.
- Reissue FIDO keys or reset passkeys for high‑risk users as needed.
- Restore necessary data into managed apps only; validate that backups are clean.
Post‑incident improvements (within 5 days):
- Conduct a short root‑cause analysis: which control failed, which alert was first, and how to detect sooner.
- Update allow lists/deny lists, DNS filtering, and training examples.
- Log the incident in the breach register; evaluate notification thresholds under Law 25/PIPEDA and consult counsel if needed.
Communications: Prepare role‑based notifications for affected users, leaders, clients (if personal data was involved), partners, insurers, and regulators where required. Provide clear, actionable guidance and anticipated timelines.
Metrics That Matter (Report Monthly)
- Coverage: Percentage of devices enrolled in MDM and MTD for eligible roles (target: 100%).
- Hygiene: Percentage of devices on latest OS major‑1 (target: ≥ 95%).
- Response speed: Mean time to quarantine a risky device after alert (target: < 15 minutes).
- Human risk: Smishing simulation click‑through rate (target: < 3%).
- Control effectiveness: Number of sideload attempts blocked; number of high‑risk permissions denied; number of risky Wi‑Fi connections prevented.
- Access resilience: Percentage of high‑risk apps protected by passkeys/FIDO keys (target: 100% of finance/admin).
Use these KPIs to drive accountability and to demonstrate continuous improvement to leadership, clients, and insurers.
30‑Day Rollout Plan (Practical and Budget‑Aware)
Week 1 – Discover and Decide
- Build the device inventory from identity and email logs; identify unenrolled devices.
- Confirm your MDM/UEM platform and shortlist an MTD provider with strong on‑device detection and MDM/SIEM integrations.
- Draft a one‑page mobile standard and BYOD addendum; pre‑brief HR and legal.
Week 2 – Configure and Pilot
- Enforce baseline policies: PIN/biometric, encryption, auto‑updates, minimum OS, no sideloading, block unknown profiles.
- Pilot MTD with executives, finance, HR, and admins. Test automated quarantine and app removal end‑to‑end.
- Connect MDM and MTD to SIEM/XDR; ensure alerts generate tickets with playbook links.
Week 3 – Expand and Educate
- Enrol sales, operations, and field teams. Roll out per‑app VPN and DNS filtering for finance/HR/ERP apps.
- Run a 10‑minute smishing refresher and a simple phishing simulation; capture click‑through metrics.
- Publish quick‑start guides for iOS and Android: reporting smishing, reviewing permissions, and removing profiles.
Week 4 – Prove and Improve
- Report KPIs to leadership; close enrolment gaps; follow up one‑to‑one where needed.
- Replace SMS OTP with passkeys/FIDO for finance/admin applications.
- Conduct a tabletop exercise: “lost CFO phone + payroll portal access” with IT, finance, HR, and leadership.
The 30‑day plan builds momentum, proves value quickly, and lays the groundwork for sustained improvement.
Closing the Mobile Security Gap
Most SMBs have robust laptop security—but phones and tablets are where business actually happens. Treat mobile as a first‑class endpoint. With MDM/UEM for control, MTD for real‑time detection and automated response, phishing‑resistant authentication, Zero Trust access, and a privacy‑respecting BYOD model, you can materially reduce risk without slowing the business. Start with high‑impact roles, measure relentlessly, and expand.
Key Links:
NIST Mobile Security Guidelines
Canada Cyber Centre: Mobile Travel Guidance
FAQ:
What’s the fastest way to cut mobile risk this quarter?
Enroll every device in MDM/UEM, deploy on-device MTD to executives/finance first, and replace SMS codes with passkeys or FIDO2 keys. Add DNS filtering and a 10-minute smishing refresher to drive quick, measurable wins.
How do we secure BYOD without invading privacy?
Use work profiles (Android) or managed apps (iOS) so corporate data lives in a container. IT sees posture, not personal content. If a device is lost or offboarded, only the work container is wiped.
What KPIs prove our mobile program is working?
Track MDM/MTD coverage (target 100%), mean time to quarantine (<15 minutes), devices on latest OS major-1 (≥95%), and smishing simulation click-through (<3%). Report monthly and act on outliers to keep momentum.
When should we notify under Law 25/PIPEDA?
If personal information may cause a “risk of serious injury,” document in the breach log and assess notification thresholds. Prepare templates in advance and coordinate with legal, privacy, and insurance when in doubt.
PROBLEM
Mobile is now attackers’ easiest path.
IMPACT
Data loss, operations disruption, legal exposure, insurer friction.
SOLUTION
Enforce MDM/UEM + on-device MTD, phishing-resistant MFA (passkeys/FIDO2), Zero Trust access, and mobile-aware IR.
CONSEQUENCE
Delay drives smishing success and session hijacks; acting now cuts incidents, speeds containment, and proves due diligence under Law 25/PIPEDA.
Our Cybersecurity Guarantee
“At Fusion Cyber Group, we align our interests with yours.“
Unlike many providers who profit from lengthy, expensive breach clean-ups, our goal is simple: stop threats before they start and stand with you if one ever gets through.
That’s why we offer a cybersecurity guarantee: in the very unlikely event that a breach gets through our multi-layered, 24/7 monitored defenses, we will handle all:
threat containment,
incident response,
remediation,
eradication,
and business recovery—at no cost to you.
Ready to strengthen your cybersecurity defenses? Contact us today for your FREE network assessment and take the first step towards safeguarding your business from cyber threats!






























































































