How Password Brute-Force Attacks Work & Best Practices to Prevent Them
What Is a Brute-Force Password Attack?
A brute-force password attack is one of the oldest and most common hacking techniques. Instead of relying on trickery or exploiting software flaws, an attacker simply tries different password combinations until the correct one is found. Think of it as a digital version of trying every key on a keyring until one opens the lock.
Modern attackers rarely do this manually. They use automated scripts, bots, and credential-cracking tools that can attempt thousands—or even millions—of guesses per second. With today’s computing power and access to cloud servers, attackers can scale these attempts cheaply and quickly.
Why It’s a Problem
Brute-force campaigns represent a serious business risk for several reasons:
Compliance and liability: A single compromised login may trigger mandatory reporting under privacy regulations like Quebec Law 25, GDPR, or HIPAA. The resulting financial penalties and reputational fallout can be significant.
Always-on threat: Automated guessing can run continuously in the background, meaning your defences are being tested 24/7, often without your awareness.
Speed and automation: Tools like Hydra, John the Ripper, or Hashcat can blast through massive lists of potential credentials in minutes, shrinking what once took weeks into hours.
Exploitation of weak credentials: Many employees still rely on predictable login details such as “Winter2025!” or reuse the same access key across multiple accounts. These habits make automated attacks far more effective than most businesses realize.
Chain reaction risks: Once intruders break into a single account, they can escalate privileges, move laterally across systems, and reach sensitive information such as financial records, intellectual property, or client data.
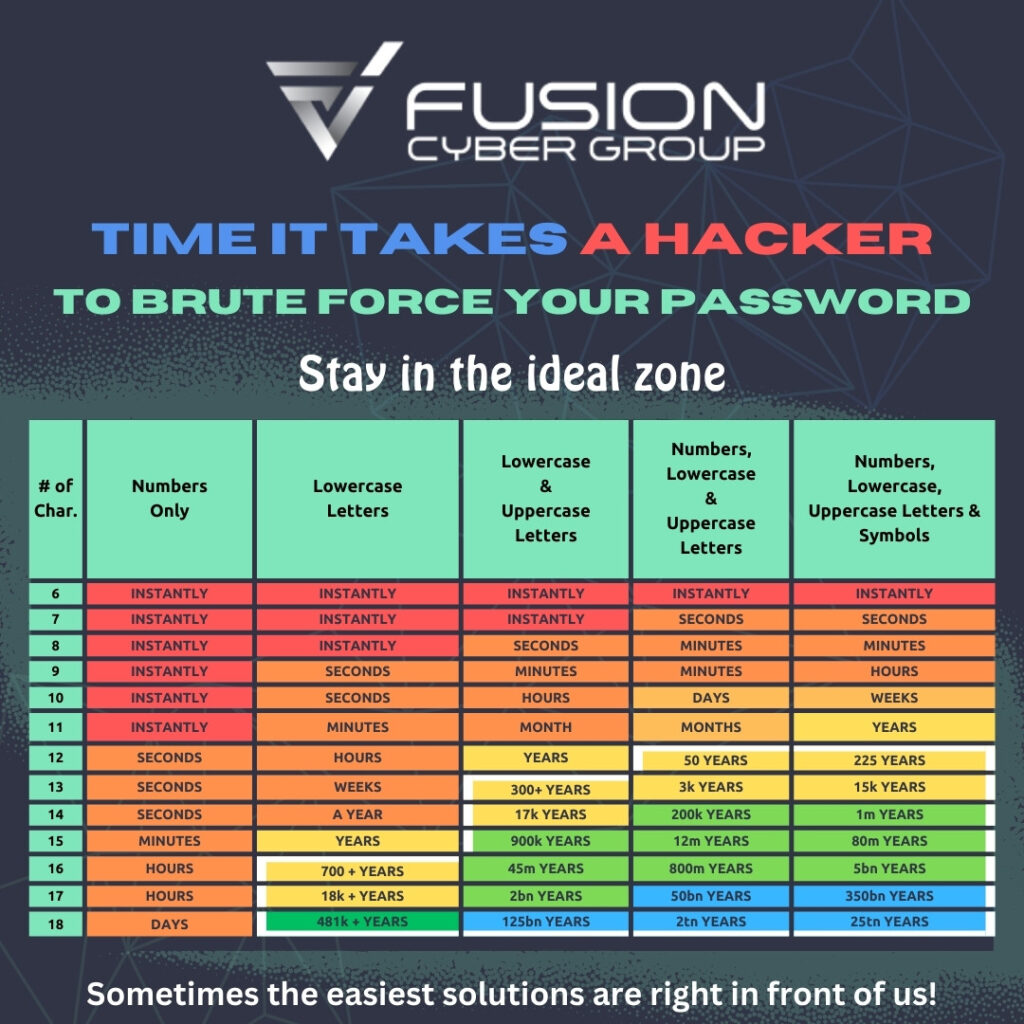
Common Methods of Brute-Force Attacks
Brute-force attacks are not one-size-fits-all. Attackers adapt their approach depending on the target, available tools, and the weaknesses they expect to find. Here are the most common methods you should be aware of:
1. Dictionary Attacks
- How it works: Attackers use precompiled lists of common words, phrases, or leaked passwords—called “dictionaries”—to guess credentials. Instead of trying random combinations, they focus on what people are most likely to use.
- Weakness exploited: Many users rely on simple passwords like “welcome123,” “qwerty,” or seasonal patterns such as “Summer2024.” Attackers also pull from large breach databases, meaning if your password appeared in a past leak, it’s probably in a hacker’s dictionary.
- Business impact: If even one employee uses a weak password, attackers can compromise accounts that may hold customer data, financial information, or privileged access.
2. Hybrid Attacks
- How it works: Hybrid attacks combine dictionary words with variations—adding numbers, capital letters, or symbols. For example, “Password1!” or “P@ssw0rd2025.”
- Weakness exploited: People assume adding a single number or special character makes a weak password strong. In reality, attackers anticipate these substitutions and bake them into automated tools.
- Business impact: Predictable “complexity rules” give a false sense of security. Hackers can often crack these passwords in seconds, bypassing policies that aren’t truly secure.
3. Credential Stuffing
- How it works: Attackers take usernames and passwords stolen from one breach and try them across other services. Since many employees reuse the same credentials for work and personal accounts, this method has a high success rate.
- Weakness exploited: Password reuse across multiple platforms.
- Business impact: A breach of an unrelated service (e.g., a social media site) can give attackers the keys to your corporate network. This “domino effect” makes credential stuffing especially dangerous for SMBs without strong identity management.
4. Rainbow Tables
- How it works: Rainbow tables are precomputed lists of password hashes. Instead of guessing each password, attackers match a stolen hash against the table until they find the original password.
- Weakness exploited: Poor password storage practices—specifically unsalted or weakly hashed passwords.
- Business impact: If your IT systems do not use salted, modern hashing algorithms (like bcrypt, scrypt, or Argon2), attackers can crack massive volumes of credentials quickly. This not only endangers employees but also customer accounts if your business hosts login systems.
Best Practices to Prevent Brute-Force Attacks

Brute-force attacks succeed when businesses rely on weak credentials and lack layered defences. The following practices form a comprehensive defence-in-depth strategy. Each addresses a different weakness that attackers exploit.
1. Use Long, Complex, and Unique Credentials or Passphrases
Login details remain the first line of defence. A short or common choice can be cracked in seconds by automated tools. Require employees to use at least 12 characters, mixing upper- and lower-case letters, numbers, and special symbols. Better yet, encourage passphrases—a string of random words like “PurpleTrain$Garden77.” These are easier to remember but much harder to guess.
- Why it matters: Complexity and length exponentially increase the time needed for a brute-force attempt to succeed.
- Business outcome: Stronger account security with minimal training investment.
2. Enforce Multi-Factor Authentication (MFA)
MFA combines something you know (a login secret), with something you have (authenticator app, hardware token) or something you are (biometric). Even if an attacker guesses or steals the credential, they cannot log in without the second factor.
- Why it matters: Studies show MFA blocks 99% of automated account compromise attempts (Microsoft, 2019).
- Business outcome: Dramatically reduced risk of unauthorized access, especially for remote access and email accounts.
3. Apply Rate Limiting and Lockout Policies
Attackers rely on speed. By limiting the number of login attempts per minute, or locking an account after several failed attempts, you slow or block automated guessing. Some organizations add CAPTCHAs or time delays between attempts.
- Why it matters: Brute-force software thrives on scale. Rate limits remove that advantage.
- Business outcome: Fewer successful automated attacks and lower server load.
4. Use Secure Hashing and Storage Practices
Never store authentication data in plain text. Instead, use hashed and salted storage with strong algorithms like bcrypt, scrypt, or Argon2. Salting ensures identical entries do not produce identical hashes, making rainbow table attacks ineffective.
- Why it matters: If your credential database is breached, secure hashing makes it nearly impossible for attackers to recover the original secrets.
- Business outcome: Lower liability, stronger compliance with privacy laws, and improved customer trust.
5. Implement Credential Monitoring and Breach Detection
Attackers often rely on stolen logins from past breaches. Use tools that monitor the dark web or credential leak repositories to detect if employee or customer accounts are exposed. Proactively reset and alert affected users.
- Why it matters: Early detection reduces the window of opportunity for attackers.
- Business outcome: Prevents secondary breaches and protects reputation.
6. Deploy a Credential Manager
Expecting staff to create and remember dozens of strong, unique logins is unrealistic. Credential managers generate, store, and autofill securely. This reduces reuse and human error.
- Why it matters: Simplifies compliance with strong authentication practices.
- Business outcome: Productivity boost and reduced helpdesk requests for reset support.
7. Secure Account Recovery Processes
Weak reset flows can undo strong defences. Ensure reset links expire quickly, require MFA, and confirm user identity through verified email or phone numbers. Avoid security questions with predictable answers.
- Why it matters: Attackers often bypass login controls by exploiting insecure reset processes.
- Business outcome: Stronger account recovery with lower fraud risk.
8. Train Users on Phishing and Social Engineering
Brute-force attacks don’t always start at the login screen. Phishing emails can trick staff into revealing credentials, which attackers then exploit with automated tools. Regular training and phishing simulations help staff spot and report suspicious messages.
- Why it matters: Human error remains the biggest cybersecurity risk.
- Business outcome: Lower chance of credential theft and fewer successful brute-force campaigns.
Risks of Not Doing This

Failing to put strong defences in place against brute-force attacks doesn’t just increase technical risk—it creates real financial, legal, and reputational damage that can threaten the survival of a business. Here’s what’s at stake.
- Data Breaches and Unauthorized Access: Brute-force attempts often provide the first foothold for cybercriminals. Once an employee’s login details are cracked, attackers can sign in as if they were legitimate users, often without raising alarms. From there, they may steal customer records, financial information, or intellectual property, and in many cases, escalate their privileges to gain control over critical systems. The danger is that even a single weak credential can open a back door into the entire organization. By the time the intrusion is detected, intruders may already have copied or corrupted sensitive data, leading to both operational disruption and long-term financial loss.
- Regulatory Fines and Legal Liability: In Canada, Quebec Law 25 requires businesses to safeguard personal information. Similar laws exist worldwide, such as GDPR in Europe and HIPAA in the U.S. If a regulator finds that a breach occurred because of poor authentication policies or the absence of MFA, the business may be subject to steep fines and mandatory reporting requirements. These penalties can easily reach into the millions, and on top of that, organizations often face lawsuits from customers or partners whose accounts were exposed. Compliance failures turn a preventable incident into a costly legal crisis, one that small and mid-sized businesses are often ill-equipped to handle.
- Reputation Damage and Loss of Customer Trust: Clients expect their information to be managed responsibly, and when a breach proves otherwise, trust disappears quickly. Even if direct financial losses are limited, reputational harm can linger for years. Competitors may use the incident to lure clients away, contracts can be cancelled, and new deals may be harder to secure. In today’s connected world, news of weak access controls spreads fast, and a reputation for poor security is difficult to repair. For SMBs especially, losing customer trust can mean a permanent loss of revenue and market position.
- Increased Incident Response and Recovery Costs: Recovering from a brute-force-driven breach is far more expensive than preventing one. The organization must pay for forensic investigations, legal consultations, customer notifications, and system remediation—all while managing business interruption. According to IBM’s 2023 Cost of a Data Breach Report, the average cost of a breach in Canada exceeds CAD $7 million. For smaller organizations, even a fraction of that number could cripple operations. Investing in proactive safeguards is not just a security best practice—it is a cost-avoidance strategy that protects long-term financial health.
Action Steps & Owners
Defending against brute-force attacks requires both technical safeguards and clear accountability. Assigning ownership ensures that best practices are not only documented but also implemented and measured. The following steps provide a practical roadmap for SMBs and enterprises alike.
1. Define and Update the Password Policy
Owner: CISO or IT Manager
Timeline: Within 2 weeks
The foundation of strong access control is a clear, enforceable password policy. This means requiring minimum lengths of 12+ characters, banning reuse, and encouraging passphrases over complex but predictable substitutions. The CISO or IT manager should publish the policy, configure enforcement in Active Directory or cloud identity platforms, and communicate expectations to staff. Success is measured through compliance checks and reduced findings in vulnerability scans.
2. Require Multi-Factor Authentication (MFA)
Owner: Security Operations / IT
Timeline: Within 1 month
MFA is one of the most effective defences against brute-force attacks. Security teams must enforce MFA across VPNs, remote desktops, email, and SaaS applications. Priority should be given to privileged and remote accounts, which are most targeted. The rollout should be tracked until MFA adoption reaches near-universal coverage.
3. Configure Lockout and Rate Limiting on Login Endpoints
Owner: DevOps / Infrastructure
Timeline: Within 2 weeks
Attackers thrive on unlimited guessing attempts. Infrastructure teams should configure lockout thresholds (e.g., temporary lock after 5 failed attempts) and introduce exponential back-off or CAPTCHAs. Logs should be monitored to ensure attackers are blocked while minimizing disruption to legitimate users.
4. Secure Password Storage
Owner: Application Security Team
Timeline: Audit now; remediate within 1 month
Applications must never store plain-text credentials. The security team should review password storage methods and migrate to strong, salted hashing algorithms such as bcrypt, scrypt, or Argon2. A successful outcome is confirmed through audits and compliance with standards like PCI DSS or ISO 27001.
5. Deploy a Password Manager and Train User
Owner: HR / Training with Security Operations
Timeline: Rollout in 1 month; training ongoing
Password managers make strong, unique passwords practical for employees. HR and IT should jointly lead deployment, provide user training, and run awareness sessions to ensure adoption. Success can be tracked by reductions in password reuse and fewer helpdesk reset requests.
6. Monitor Breach Notifications and Set Up Alerts
Owner: Threat Intelligence / Security Operations
Timeline: Within 2 weeks
Continuous monitoring of the dark web and breach databases helps detect stolen credentials early. Security teams should set up automated alerts and workflows for resetting compromised accounts. The metric of success is how quickly exposed credentials are identified and remediated before attackers exploit them.
Conclusion
Password brute-force attacks remain one of the simplest techniques in an attacker’s toolbox, yet they are also among the most damaging when left unchecked. The good news is that they are highly preventable. Organizations that enforce strong password policies, deploy multi-factor authentication, and secure their password storage drastically reduce the chances of a successful compromise. Adding measures such as rate limiting, credential monitoring, and user training creates a layered defence that frustrates attackers and forces them to move on to easier targets.
For business leaders, the message is clear: the cost of prevention is a fraction of the cost of recovery. Investing in these safeguards not only lowers the risk of data breaches and regulatory penalties but also demonstrates to customers, partners, and regulators that security is taken seriously. In today’s market, trust is a competitive advantage, and strong credential security is one of the clearest ways to earn it.
By acting on the steps outlined in this guide, your organization can transform brute-force attacks from a serious threat into a manageable risk. The result is greater resilience, stronger compliance, and the confidence that your systems and data are protected.
Protecting access to your systems is no longer optional—it is a business-critical responsibility that defines resilience in the digital age.
👉 Ready to strengthen your defences? Contact Fusion Cyber Group today
Featured links:
NIST SP 800-63-4: Digital Identity Guidelines
OWASP Authentication Cheat Sheet
FAQ:
How do brute-force attacks work?
Brute-force attacks systematically try different login combinations until one works. Attackers use automated tools that can attempt thousands—or even millions—of guesses per second.
Why are brute-force attacks dangerous for SMBs?
Small and mid-sized businesses often lack advanced defences. A single compromised account can expose financial data, customer records, or entire systems, leading to costly breaches and regulatory penalties.
What is the best way to stop brute-force attacks?
The most effective approach is layered security: strong credential policies, multi-factor authentication (MFA), account lockouts, secure password storage, and ongoing user training.
How common are brute-force attacks today?
They are still one of the most common attack methods. Automated bots constantly probe login portals around the world, making every business a potential target 24/7.
Do password managers really help?
Yes. Password managers generate and store strong, unique credentials for each account, reducing human error, preventing reuse, and making brute-force attacks far less effective.
Our Cybersecurity Guarantee
“At Fusion Cyber Group, we align our interests with yours.“
Unlike many providers who profit from lengthy, expensive breach clean-ups, our goal is simple: stop threats before they start and stand with you if one ever gets through.
That’s why we offer a cybersecurity guarantee: in the very unlikely event that a breach gets through our multi-layered, 24/7 monitored defenses, we will handle all:
threat containment,
incident response,
remediation,
eradication,
and business recovery—at no cost to you.
Ready to strengthen your cybersecurity defenses? Contact us today for your FREE network assessment and take the first step towards safeguarding your business from cyber threats!
In today’s digital age, passwords are the first line of defense against cyber threats. They protect our personal information, financial data, and online identities. However, many people still use weak passwords or reuse the same password across multiple accounts, leaving them vulnerable to cyber attacks. In this article, we will discuss the best practices for password management to help you keep your information safe.






























































































