Sharing emails and links seems harmless. It isn’t.
One forwarded thread or public link can expose client data, logins, or finance details. Criminals rely on speed and habit—people click before they think. This guide shows how to share safely, what to watch for, and what to do if something slips.
Email and link sharing are still the fastest paths to business compromise. Phishing, credential abuse, and vulnerability exploits account for the majority of breaches globally. In Canada, reported fraud losses reached $638M in 2024. Your best defence: reduce risky sharing behaviours, harden identity (adopt phishing‑resistant MFA), and use secure sharing workflows with data loss prevention (DLP). This article updates our 2024 guidance with new threats like QR‑code phishing (“quishing”), adversary‑in‑the‑middle (AiTM) kits, and phishing‑as‑a‑service platforms.
Understanding the risks
What counts as sensitive information?
- Client and employee details (names, addresses, SINs)
- Financial information (invoices, banking changes, payroll)
- Credentials (passwords, backup codes, API keys, OAuth tokens)
- Contracts, pricing, proposals, legal and HR files
Sensitive information also includes indirect identifiers that seem harmless on their own but reveal people or accounts when combined: project codes tied to a client, ticket numbers, shipment IDs, calendar invites (topics, attendees), and even email signatures. Operational details—server names, VPN endpoints, internal URLs, device serials, Wi-Fi SSIDs—help attackers map your environment and craft convincing lures.
Treat links that grant access as sensitive, too. “Anyone-with-the-link” shares, pre-authenticated “magic links,” and document previews can be forwarded outside your control. Session cookies and recovery codes are as valuable as passwords; never paste them into chats or emails. Watch out for metadata in documents and images (author, timestamps, GPS) and for hidden tracked changes/comments in Word, Excel, and PDF files. Screenshots and screen recordings often capture more than intended (tabs, bookmarks, meeting IDs).
When uncertain, default to Confidential and remove quoted history and unnecessary recipients before you send.
What are malicious websites?
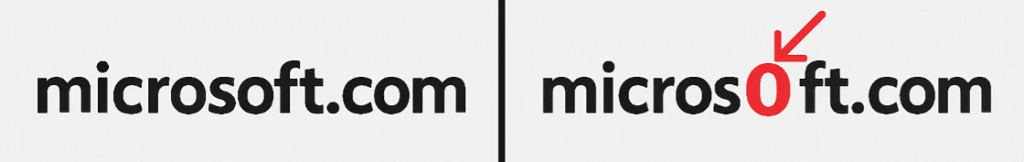
They’re fake or compromised pages designed to:
- Steal credentials (look-alike login pages)
- Plant malware (drive-by downloads)
- Trick you into payments or data sharing (spoofed portals)
Modern scams go beyond obvious misspellings. Attackers use look-alike domains (e.g., “micros0ft.com”), homoglyphs (letters that look the same), URL shorteners, and QR codes to hide real destinations. Some pages show a padlock (HTTPS) and a clean design, then prompt for a “security re-login,” request an OAuth consent (“Allow this app to read your email”), or present a fake captcha to seem legitimate. Others are compromised legitimate sites or malvertising results placed at the top of search engines (SEO poisoning). A single click can hand over passwords and session tokens via “adversary-in-the-middle” kits.
Quick checks: hover/long-press to preview URLs, expand short links, read the root domain (just before “.com/.ca”), and be sceptical of urgent payment or login prompts. If in doubt, type the known address manually or open the site from your bookmarked portal instead of clicking the link.
The 2025 Threat Picture

1) Business Email Compromise (BEC)
Impersonation of executives, suppliers, or legal counsel to redirect payments or share confidential data. Attackers study LinkedIn, vendor portals, and email footers to time convincing requests.
Tell‑tale signs: urgent wire changes, new banking details, secrecy, “are you at your desk?” pretexts, invoice PDFs hosted on odd domains.
Canadian context: CAFC reports repeated high‑value BEC cases; law‑firm and professional‑services targets are common across provinces.
2) QR‑Code Phishing (Quishing)
Malicious QR codes in parking meters, restaurant tables, emails, and PDFs route users to fake login pages or malware. Many email filters don’t scan images as strictly as URLs.
Defences: verify the destination URL on‑screen before authenticating; prefer official apps; treat random QR codes like unknown USB keys.
3) AiTM & Session Hijacking
Attackers insert a proxy between you and Microsoft 365/Google to capture passwords and session cookies. Once a cookie is stolen, attackers skip MFA and operate as you.
Defences: phishing‑resistant MFA (security keys or device‑bound passkeys), Conditional Access, continuous sign‑in risk evaluation, token protection, and short‑lived sessions.
4) Phishing‑as‑a‑Service (PhaaS)
Turnkey kits (templates, hosting, SMS/email spoofing, even “customer support”) make enterprise‑grade phishing accessible to low‑skill actors. Expect cleaner grammar, local branding, and regional spellings.
Common Scenarios Where Risks Arise
1. Forwarding without redaction: Quoted email chains often expose signatures, mobile numbers, calendar links, case IDs, and tracking URLs.
2. Reply‑all & autocomplete mistakes: Similar contact names cause misdirected emails. BCC/CC misuse leaks addresses and deal context to unintended parties.
3. Sharing links on social or chat: That Google Drive/SharePoint link may be open to “anyone with the link.” Screenshots of email threads can reveal ticket numbers and internal URLs.
4. Public Wi‑Fi & personal devices: Interception, outdated OS, or sideloaded apps increase risk; SMS 2FA can be SIM‑swapped.
5. Calendar & e‑signature lures: Fake Microsoft/Adobe/DocuSign invites route to AiTM pages.
Safe‑Sharing Playbook
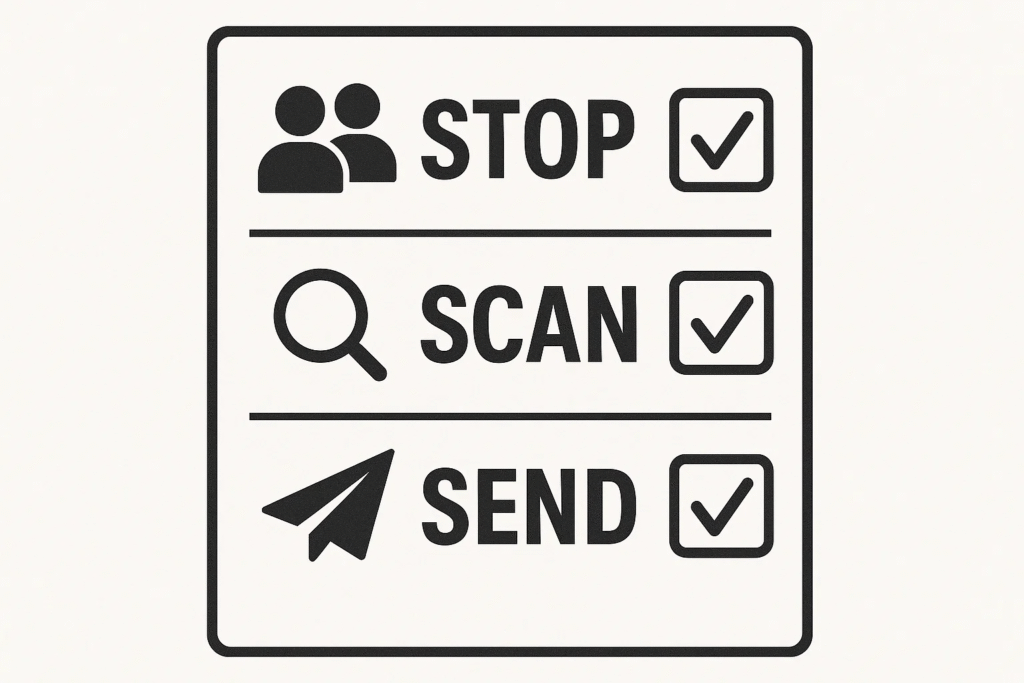
A. Pre‑Send STOP • SCAN • SEND Checklist
1. STOP
- Who exactly is on To/CC? Remove auto‑filled “near‑matches.”
- Is any sensitive information included? Strip footers/signatures from quoted chains.
2. SCAN
- Hover/long‑press to preview URLs; expand shortened links.
- Attachments from outside? Open in a cloud sandbox/Safe Documents.
3. SEND
- Use a managed link (SharePoint/OneDrive/Google Drive) with view‑only, expiry, and password.
- Share credentials through a password manager’s sharing feature—never by email or chat.
B. Use Secure Channels by Default
Documents: Share from your company SharePoint/OneDrive/Google Drive so you can grant, change, and revoke access at any time.
- Use named recipients only (no “anyone with the link”). Require sign-in.
- Set expiry dates (e.g., 7–14 days) and auto-expire external guests.
- Turn on watermarking and block download for view-only links to reduce leaks and screenshots.
- Keep version history and enable file restore so mistakes are reversible.
- For sensitive files, apply Sensitivity Labels/Rights Management (e.g., “Confidential—No Forward/Print”) so controls travel with the file, even offline.
- Prefer File Request or secure client portals over email attachments when collecting documents from customers.
Chat: Use corporate Teams/Slack with external guest controls and DLP (Data Loss Prevention).
- Allow external guests by invitation only, with auto-expiry and restricted file uploads.
- Create private channels for finance/legal; block personal accounts.
- Turn on message retention and eDiscovery for audits and investigations.
Email: Enforce TLS transport encryption as a baseline and use confidential/encrypt options for sensitive threads.
- Apply a “Confidential” sensitivity label that triggers automatic DLP scanning (e.g., block or justify sends containing SINs/banking details).
- Use secure message portals for outside recipients who lack compatible mail systems.
- Disable auto-forward to external by default; allow exceptions via approval.
Identity & devices (make it stick):
- Require sign-in and compliant devices (company or enrolled BYOD) before users can open shared links.
- Use Conditional Access (block risky locations, step-up MFA for sensitive labels).
- Train teams: share links from the drive, never attach live spreadsheets with client data, and always set expiry + view-only for external recipients.
These defaults make sharing auditable, revocable, and consistent, turning “oops” moments into manageable events instead of breaches.
C. Harden Identity & Access
GOOD – MFA everywhere; disable SMS where possible; unique passwords in a password manager
BETTER – Conditional Access, location/device risk policies; number‑matching push; disable legacy protocols (IMAP/POP)
BEST – Phishing‑resistant MFA, device compliance required, token protection, continuous access evaluation
D. Make Emails Verifiable
- Authenticate your domain properly.
- SPF: publish a tight record that lists only authorised senders (M365, your marketing platform, service desk). Remove legacy include’s and unknown IPs.
- DKIM: enable for all sending services with 2048-bit keys; rotate keys annually.
- DMARC: start at p=quarantine; pct=25 with RUA/RUF reporting so you see who’s spoofing you, then move to p=reject; pct=100 once aligned. Use SP/ADKIM/ASPF=strict to cover subdomains and tighten alignment.
- Show who you are.
- BIMI: once DMARC is at enforcement (quarantine/reject), publish a verified SVG logo (consider VMC where supported) so recipients see visual trust cues.
- Help users see risk at a glance.
- Add [EXTERNAL] tagging and an inline banner for first-time or newly-registered domains (e.g., “Caution: first email from this domain in 12 months”).
- Enable display-name impersonation and look-alike domain detection (e.g., “micros0ft.com”).
- Neutralise payloads and links.
- Turn on time-of-click protection (Microsoft Safe Links / Google URL scanning), including inside Office/PDFs and mobile clients.
- Enable Safe Attachments / sandbox detonation (dynamic analysis) for unknown files; quarantine or strip risky types.
- Use ZAP/Zero-Hour Auto Purge to retract malicious emails discovered after delivery.
- Block auto-forwarding to external by default and alert on suspicious inbox rules.
- Monitor and iterate.
- Review DMARC reports weekly, fix third-party senders, and decommission unused mail streams. Track impersonation blocks, ZAP recalls, and first-seen domain alerts as KPIs.
E. Data Loss Prevention (DLP)
- Define what to protect: Patterns for Canadian SIN (###-###-###), banking strings (transit/institution/account), payment card data, health/HR files, client IDs, and contract numbers. Use keyword proximity (“SIN”, “transit no.”) to reduce false positives.
- Label and control automatically: Auto-apply Sensitivity Labels (e.g., Confidential – Client Data) that enforce no forward/print, watermarking, and encryption. Labels should travel with attachments across email, Teams/Slack, and cloud storage.
- Inspect everywhere data lives: Enable DLP for Exchange/SharePoint/OneDrive/Teams/Slack; include OCR for images/PDF scans and Exact Data Match (EDM) for your client/account tables. Extend to Endpoint DLP to stop copy-to-USB, print, and clipboard leaks.
- Coach, don’t just block: Use just-in-time tips: when a user tries to email SINs externally, show a clear prompt to remove data, switch to a secure portal, or provide a business-justification override.
- Govern exceptions: Require manager/security approval for overrides; log all exceptions, review weekly, and tune policies (thresholds, allowed domains). Start in audit mode, then move to block with override, and finally hard block for high-risk data.
- Measure and maintain: KPIs such as incidents by policy, top violators (by department), false-positive rate, mean time to review, and percent of data auto-labeled. Re-test policies quarterly as workflows and templates change.
Tools and Technologies to Enhance Security
Email security & DNS filtering
An email security layer should do more than catch obvious spam; it should inspect sender authentication (SPF, DKIM, DMARC), detect brand impersonation, and rewrite links so they’re checked again at the moment of click. Pair that with DNS filtering at the network and device level. Protective resolvers block known-bad domains, typo-squats, and newly registered look-alikes before the browser even opens, which dramatically reduces the chance of a successful phish. When attachments arrive, modern gateways detonate files in a sandbox to observe behaviour safely, then quarantine anything suspicious.
EDR/XDR & 24/7 SOC
Assume someone will eventually click. That’s where endpoint detection and response (EDR) and its big sibling, extended detection and response (XDR), earn their keep. These tools watch process behaviour, registry changes, script execution, and network calls across endpoints and cloud workloads. If malware launches or a legitimate tool is abused (PowerShell, RMM agents), EDR/XDR can isolate the device, kill the process, and roll back changes. The difference between “scare” and “breach” is often the speed of that automated containment.
Behind the scenes, a 24/7 security operations centre (SOC) ties it all together. Analysts triage alerts, correlate signals across email, endpoints, identity, and cloud apps, and run playbooks to contain threats while you sleep. For SMBs, this round-the-clock coverage is the most practical way to get enterprise-grade vigilance without building an internal team.
Password managers
A business-grade password manager gives every user a private vault, lets teams share credentials without revealing them, and generates unique, long passwords by default. Audit logs show who accessed what and when, and off-boarding is as simple as revoking vault access. Better yet, make stolen passwords useless. Security keys and passkeys (FIDO2/WebAuthn) bind login to the user’s device and a specific site, so credential replay and adversary-in-the-middle attacks fail outright. They’re fast, easy on users, and ideal for finance and admin roles.
Security keys/passkeys
Better yet, make stolen passwords useless. Security keys and passkeys (FIDO2/WebAuthn) bind login to the user’s device and a specific site, so credential replay and adversary-in-the-middle attacks fail outright. They’re fast, easy on users, and ideal for finance and admin roles.
Security awareness training
Finally, technology works best when people know how to use it. Short, frequent security awareness sessions and realistic phishing simulations build habits—hovering links, challenging unusual requests, and reporting quickly. Reinforce wins and measure click-through and report rates to prove progress.
If you clicked or shared by mistake
First, isolate without destroying evidence. Disconnect the device from Wi-Fi and wired networks or enable airplane mode, but do not power it off—memory and logs are valuable for forensics. If you’re on a corporate laptop or phone, notify IT so they can remotely isolate the endpoint in EDR while preserving data. Make a quick note of what happened (time, sender, subject, link or file name) so investigators can trace the path.
Next, protect identity. From a different, clean device, change passwords for any account you may have exposed and force a sign-out of all sessions. Revoke remembered devices and app passwords, and re-register MFA if prompted. In Microsoft 365/Google Workspace, review Security > Authorized Apps and remove unfamiliar OAuth grants—malicious apps can keep reading mail even after a password change. Watch for oddities such as new inbox rules, auto-forward to external addresses, or deleted-item rules that hide attacker activity; remove anything you didn’t set.
Lock down shared content. In your drive (SharePoint/OneDrive/Google Drive), locate anything you just shared and switch access to named recipients only, set expiry (or revoke if unnecessary), and disable download for view-only. Search for “Anyone with the link” items and tighten them. If a public link was emailed broadly, replace it with a managed link and post a corrected message, asking recipients to delete the earlier version.
Now check the device. Run a full EDR/antivirus scan and follow quarantine prompts. If EDR flags suspicious processes (PowerShell, script runners, unknown browser extensions), let the SOC/IT complete containment and collect artifacts. Don’t manually delete the original phishing email—report it using the built-in “Report phish” button so security tools can retract copies across the organization.
Escalate promptly. Tell your Privacy Officer or IT lead. If any personal information may have been exposed, they’ll assess notification and reporting requirements under Canadian privacy law and advise on client communication. If money or invoices are involved, call your bank immediately to attempt a recall or hold and report the incident to local authorities. Preserve evidence: take screenshots of messages and URLs, save headers, and keep timeline notes. Speed matters—the first hour is where you can turn a mistake into a contained event rather than a breach.
Conclusion
It is essential to be cautious when sharing emails and links to maintain a low-risk threat factor. Verifying content, using secure channels, and educating contacts are vital steps in this process. Implement the discussed practices and tools to enhance your security and encourage your contacts to do the same, creating a safer digital environment for everyone. Remember, vigilance is key in protecting yourself and your contacts from potential cyber threats. By being cautious and proactive, you can significantly reduce the risk of data breaches and other cyber incidents.
Need this handled end-to-end—secure sharing, phishing-resistant MFA, DLP, and 24/7 response—without adding headcount?
Fusion Cyber delivers these controls as managed services for SMBs—SOC, MDR/EDR/XDR, email/DNS filtering, DLP, awareness training, dark web monitoring, and incident response—backed by our financial Cybersecurity Guarantee for fully onboarded clients. Explore our solutions
Related Reads:
The Human Element: Security Awareness Training
AI‑Enhanced Phishing: What’s New
Session Hijacking 2.0 (AiTM/BitM)
FAQ:
Is it safer to attach a PDF than to share a link?
Not by default. PDFs can contain embedded links or sensitive metadata, and attachments spread beyond your control. A managed cloud link with named recipients, view-only, expiry, and watermarking is usually safer and more auditable.
We already have MFA—why push for security keys or passkeys?
App-based MFA stops many attacks but can be phished or “approved” by mistake. Security keys/passkeys (FIDO2/WebAuthn) are phishing-resistant—they bind the login to your device and the real site, so adversary-in-the-middle kits and fake pages fail.
When should we use email vs. chat vs. a portal for documents?
Use a secure client portal or managed share link for any file with client data, finance details, or credentials. Keep quick, low-risk coordination in Teams/Slack. Email is fine for scheduling or summaries—avoid attachments with live data.
How do we quickly verify if a link is safe?
Hover/long-press to preview, read the root domain carefully, expand shortened URLs, and be sceptical of urgency. If it requests a login or payment, type the known address into your browser or use a bookmark instead of clicking.
What’s the first thing to do if someone clicked?
Isolate the device (airplane mode—but don’t power it off), change passwords from a clean device, revoke sessions, remove public links, and report it with the built-in “Report phish” button. Notify IT/Privacy immediately to assess next steps.
Our Cybersecurity Guarantee
“At Fusion Cyber Group, we align our interests with yours.“
Unlike many providers who profit from lengthy, expensive breach clean-ups, our goal is simple: stop threats before they start and stand with you if one ever gets through.
That’s why we offer a cybersecurity guarantee: in the very unlikely event that a breach gets through our multi-layered, 24/7 monitored defenses, we will handle all:
threat containment,
incident response,
remediation,
eradication,
and business recovery—at no cost to you.
Ready to strengthen your cybersecurity defenses? Contact us today for your FREE network assessment and take the first step towards safeguarding your business from cyber threats!






























































































